
Architecting the Ultimate Hybrid Security Homelab in 2026: A Blueprint for DevSecOps & Zero Trust
A deep dive into building a code-managed, Zero Trust homelab using Terraform, Ansible, and AWS Site-to-Site VPN.
Read Article →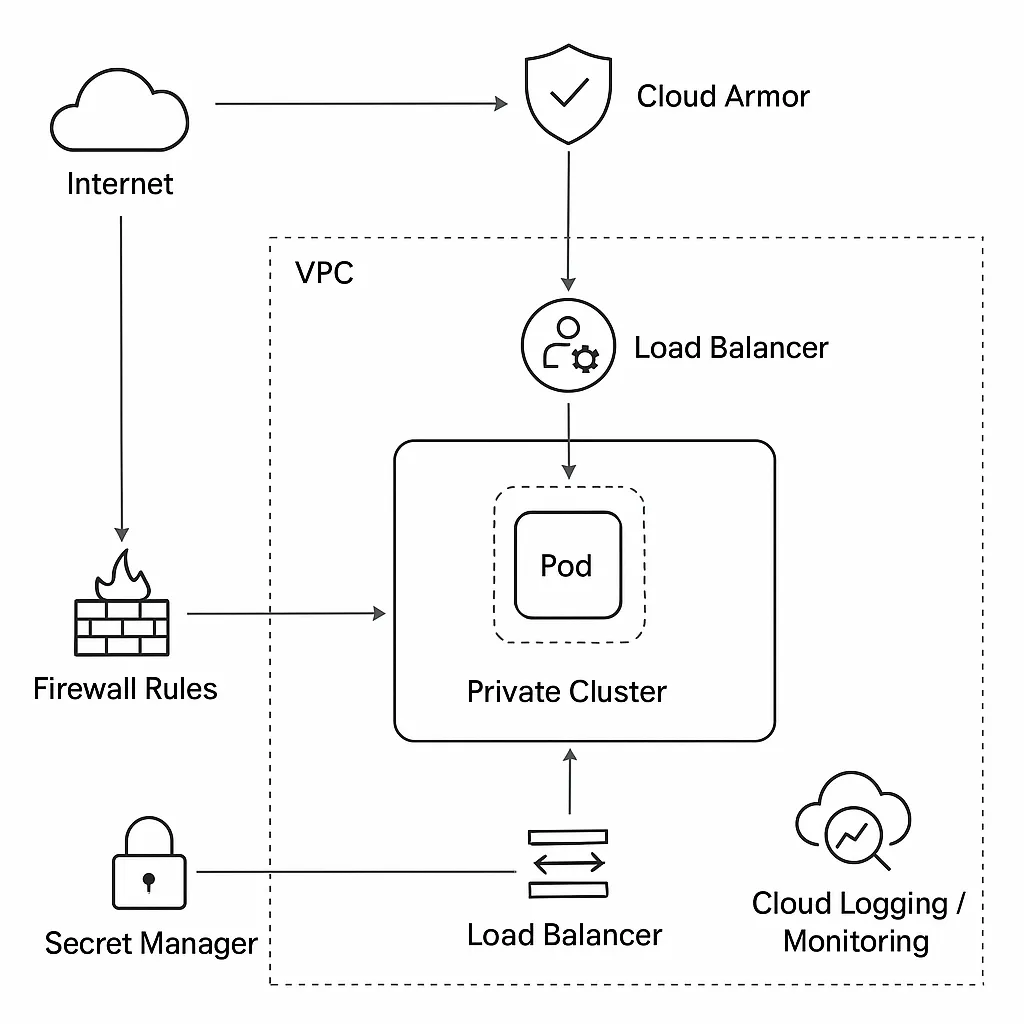
Secure GKE Deployment: Hardening Kubernetes on Google Cloud
Architecting a hardened GKE web application pipeline using Cloud Armor, Private Clusters, Workload Identity, and VPC Service Controls.
Read Article →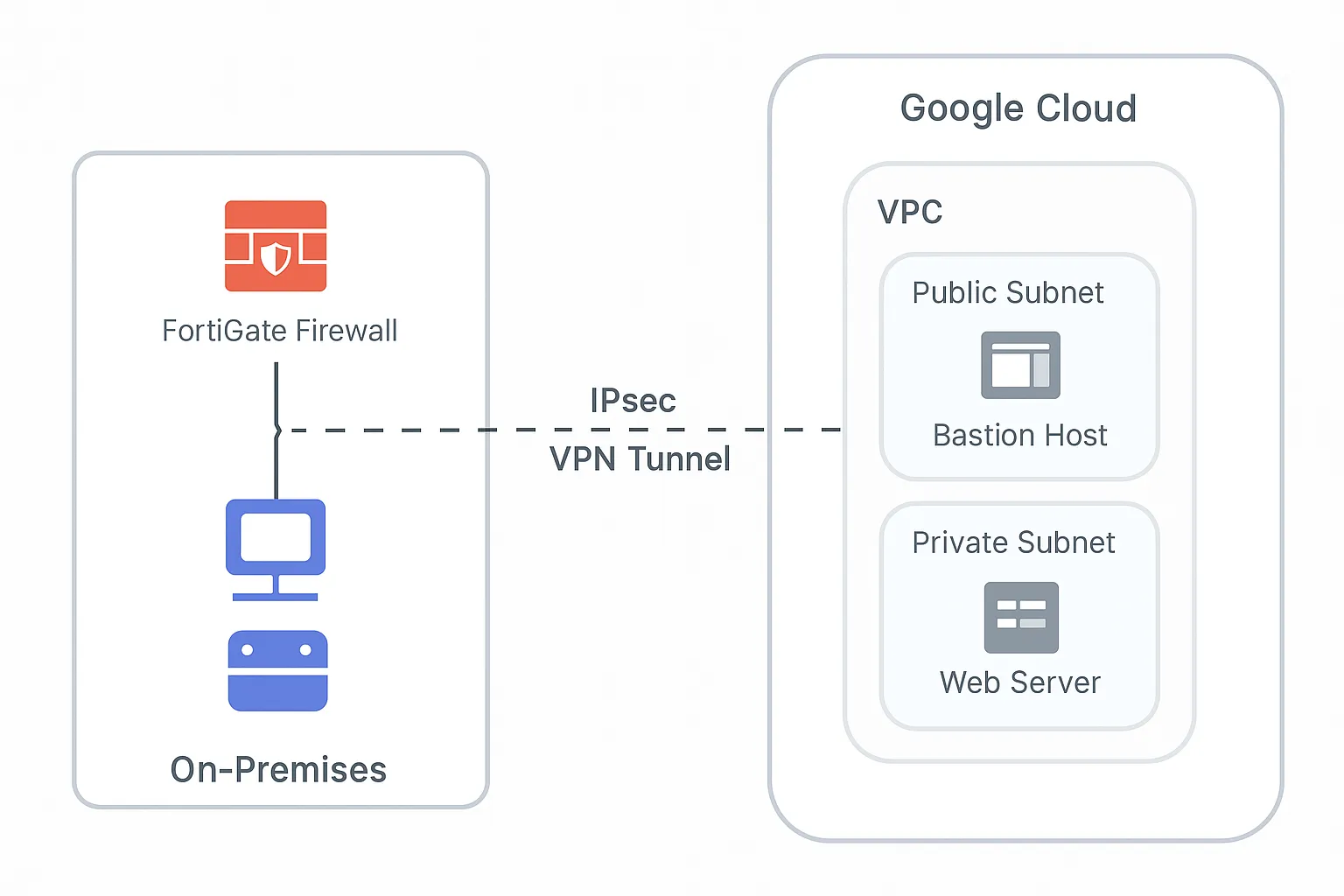
Hybrid Cloud Security: Connecting Fortinet On-Prem to GCP
Designing a resilient, encrypted hybrid cloud architecture connecting on-premises Fortinet appliances to Google Cloud Platform using IPSec VPN and BGP.
Read Article →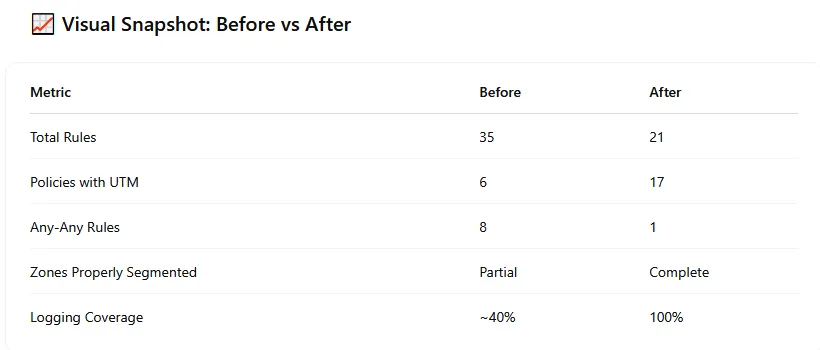
Fortigate Firewall Optimization: Reducing Attack Surface by 40%
A case study on auditing and hardening a Fortigate 60F infrastructure, resulting in a 40% reduction in firewall rules and implemented UTM profiles.
Read Article →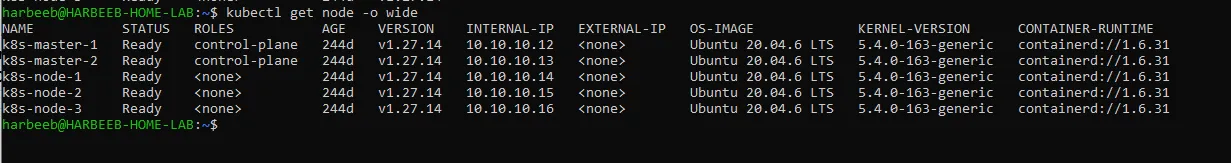
Building a Secure Kubernetes Cluster with Fortigate & Hyper-V
A step-by-step guide to deploying a high-availability Kubernetes 1.27 cluster on Hyper-V, using Fortigate for Load Balancing, Firewalling, and DHCP.
Read Article →