Hybrid Cloud Security: Connecting Fortinet On-Prem to GCP
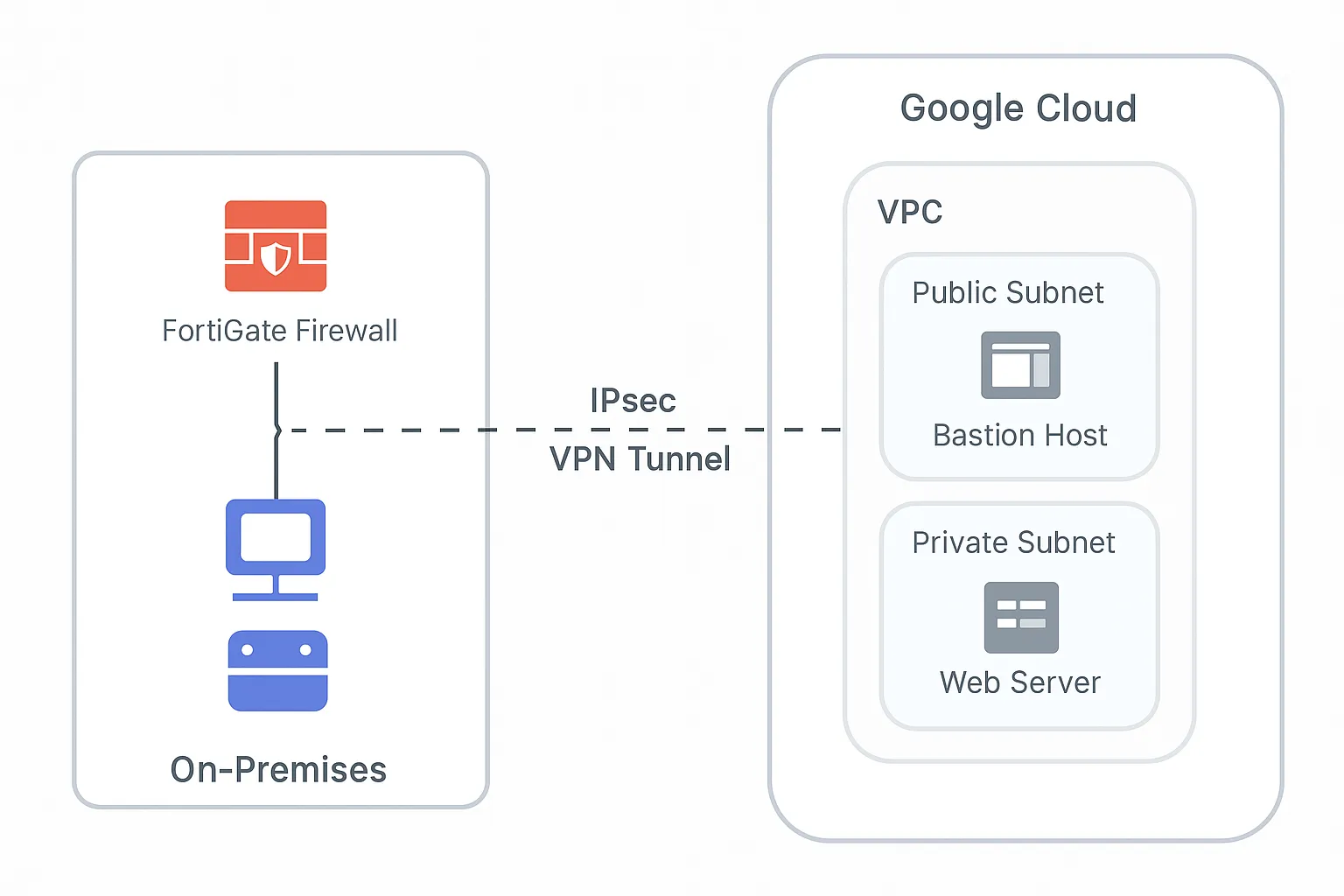
Table of Contents
Hybrid Cloud Security: Fortinet & GCP
This project demonstrates the design and implementation of a secure Hybrid Cloud architecture. The goal was to establish a resilient and encrypted connection between a customer on-premises network (utilizing Fortinet appliances) and the Google Cloud Platform (GCP) through an IPSec VPN tunnel.
The setup incorporates proper network segmentation, routing configurations, and robust firewall policies, adhering to industry best practices for hybrid cloud security.

Key Components & Configuration Highlights
- On-Premises: Configured the network security appliance (FortiGate firewall) to act as the local gateway.
- Google Cloud VPC: Designed and deployed a custom mode Virtual Private Cloud (VPC) within GCP.
- Secure VPN Connectivity: Established a secure IPSec VPN tunnel (utilizing BGP for dynamic routing) between the FortiGate and the Google Cloud VPN Gateway.
- Network Segmentation: Created two distinct subnets within the GCP VPC (public and private) to enforce security zones.
- Granular Firewall Policies: Implemented specific firewall rules on FortiGate and GCP to control traffic flow, adhering to the principle of least privilege (allowing only necessary ports and IPs).
- Bastion Host: Deployed a bastion host within the public subnet in GCP for secure remote administration access to private resources.
- Monitoring & Visibility: Integrated FortiView (on the FortiGate) and GCP Logging for comprehensive monitoring and troubleshooting capabilities.
- Routing & DNS: Advertised the appropriate Cloud DNS IP address via GCP BGP routing to allow internal DNS resolution using GCP Cloud DNS and FortiGate DNS forwarding.
Testing & Validation
The successful establishment of the Hybrid Cloud Security architecture was rigorously tested and validated through:
- VPN Status Verification: Verified the IPSec VPN tunnel status using FortiGate CLI commands and the GCP Console.
# FortiGate CLI diagnose vpn tunnel list # GCP Console gcloud compute vpn-tunnels describe - Connectivity Testing: Performed ICMP pings, port scans, and application-layer tests initiated from both the on-premises and GCP environments.
- Packet Analysis: Conducted packet capture analysis on FortiGate and GCP to confirm traffic encryption and adherence to defined network paths.
Outcomes & Value Delivered
Business Impact
This project delivered a secure and reliable hybrid cloud infrastructure, enabling seamless connectivity and data flow between on-premises and Google Cloud environments. Implementing robust and encrypted communication channels enhanced data security and reduced the risk of unauthorized access. The strategic network segmentation and granular firewall policies established a strong security posture, minimizing potential attack surfaces and improving overall compliance. This solution provides a scalable foundation for future cloud expansion while maintaining consistent security controls across both environments.
Key Security Gains
Implementing an IPSec VPN ensured end-to-end encryption, safeguarding data in transit. Using Fortinet’s UTM profiles and granular firewall policies provided advanced threat protection against malware, intrusions, and malicious web traffic. Network segmentation limited the blast radius of potential security incidents, and the design adhered to the principle of least privilege, minimizing unnecessary access and strengthening the overall security posture.
Skills Leveraged & Enhanced
This project directly utilized and further strengthened my expertise in:
- Hybrid Cloud Architecture: Designing and implementing cohesive security strategies across disparate environments.
- Fortinet Firewall Mastery: Advanced configuration, VPN deployment, and UTM profile optimization for enhanced security.
- Google Cloud Networking Security: Implementing secure VPCs, firewall rules, and VPN gateways within GCP.
- Secure Network Design: Applying principles of network segmentation, routing, and access control to build resilient and secure infrastructures.
- Troubleshooting & Validation: Proficiently diagnosing and verifying secure connectivity and policy enforcement across hybrid environments.
- Security Policy Implementation: Translating security requirements into practical and granular firewall rules and security profiles.