Architecting the Ultimate Hybrid Security Homelab in 2026: A Blueprint for DevSecOps & Zero Trust

Table of Contents
Introduction
As 2026 begins, the definition of a security engineer has changed. The role is no longer centered on manually configuring systems or reacting to alerts in isolation. Today’s security work sits at the intersection of cloud architecture, automation, identity governance, and operational decision-making.
Certifications provide a common language, but fluency comes from designing and operating real systems—systems that fail, scale, and require tradeoffs.
This year, I rebuilt my homelab as if it were a greenfield enterprise deployment. Rather than refreshing tools, I focused on architecting a platform that reflects the environments I work with professionally: hybrid by design, managed through code, and secured through segmentation and identity.
This post walks through the architecture, the reasoning behind key decisions, and how this lab supports both technical depth and higher-level security thinking.
Architecture Overview: Hybrid by Design
Modern environments are rarely confined to a single network boundary. To reflect that reality, this lab was designed as a hybrid environment from day one.
Hybrid Connectivity (On-Prem + Cloud)
At the core is a site-to-site IPsec VPN between an on-premise pfSense firewall and an AWS VPC.
This allows the lab to simulate real enterprise data flows:
- On-premise Wazuh ingests logs from cloud workloads
- Identity services span local and cloud-hosted systems
- Network boundaries are enforced, but no longer absolute
This mirrors how organizations actually operate today—distributed, interconnected, and borderless by default.
Infrastructure as Code: Designing for Repeatability

One of the most important shifts in this lab was treating infrastructure as software.
- Terraform is used to provision cloud resources and define core infrastructure components.
- Ansible handles configuration management across Linux systems, defensive tooling, and intentionally vulnerable hosts.
The intent is not speed for its own sake, but predictability. If a system is compromised or misconfigured during testing, it is rebuilt—not manually repaired.
From an operational perspective, this enables:
- Faster recovery
- Clear change history
- Reduced configuration drift
- Easier collaboration and review
This is the same mindset required in environments that must scale, pass audits, or survive personnel changes.
Core Security Building Blocks
1. Identity as the Control Plane
Identity is the foundation of the lab.
An on-premise Windows Server 2022 Domain Controller provides centralized authentication, DNS, and policy enforcement. An internal Certificate Authority issues trusted certificates for services and enables encrypted communication (LDAPS, HTTPS) across the environment.
Rather than treating PKI as an afterthought, it is used deliberately to establish trust boundaries—something many environments only appreciate once certificates expire or fail unexpectedly.
2. Unified Observability and Detection
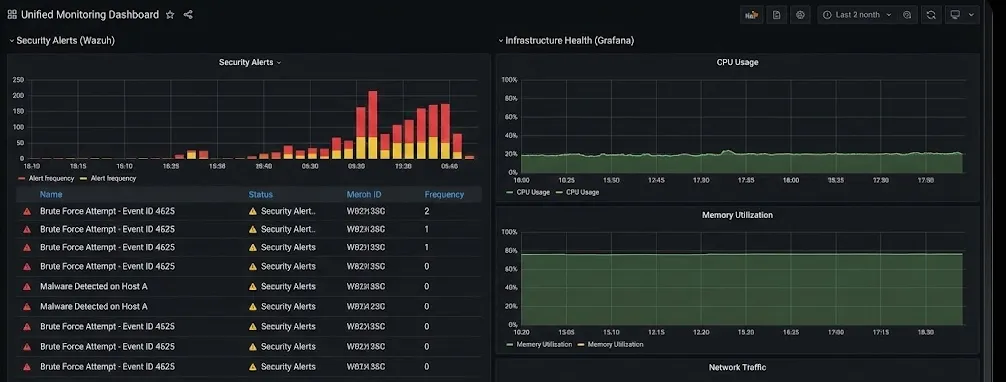
Security begins with visibility, but visibility alone is not enough.
- Wazuh serves as the SIEM, collecting host-based telemetry from both on-prem and cloud workloads.
- Suricata provides network-level insight at the firewall.
- Prometheus and Grafana track infrastructure health and performance metrics.
This layered approach allows correlation between system behavior, security events, and resource usage—turning logs into context rather than noise.
3. Segmentation as a First-Class Control
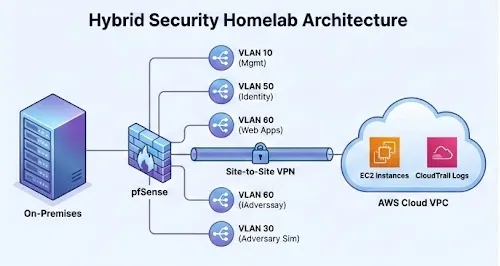
Network segmentation is enforced using pfSense and purpose-built VLANs:
- VLAN 10 – Management: Monitoring, CI/CD pipelines, and control-plane services
- VLAN 60 – Web and Application Zone: Applications targeted by automated and manual testing
- VLAN 30 – Adversary Simulation: A contained sandbox for malware detonation and attack emulation
Nothing communicates by default. Access paths are explicit, logged, and reviewed.
This structure supports both defensive validation and realistic attack simulation without collapsing trust boundaries.
4. AI as an Analyst Multiplier, Not a Replacement
AI is introduced carefully and intentionally.
Sanitized logs and alert context are fed into a local LLM to assist with:
- Pattern recognition during investigations
- Hypothesis generation in threat hunting
- Summarization of complex alert chains
The goal is efficiency, not autonomy. Human judgment remains central, with AI acting as an analytical assistant rather than a decision-maker.
Security Is Ultimately About Tradeoffs
One of the most valuable aspects of this lab is deciding what not to implement.
Every control is evaluated against:
- Operational complexity
- Maintenance cost
- Signal-to-noise ratio
- Actual risk reduction
This reflects real-world security leadership, where time, people, and budget are finite—and perfect security is neither realistic nor necessary.
Conclusion
Building a homelab teaches tools. Architecting one teaches judgment.
By combining hybrid connectivity, infrastructure as code, identity-centric security, observability, and automation, this environment supports both deep technical learning and architectural thinking. It reflects how modern security teams design, operate, and govern systems—not just how they deploy them.
Upcoming posts will dive deeper into specific components, including infrastructure-as-code workflows, and Active Directory hardening.