Secure GKE Deployment: Hardening Kubernetes on Google Cloud
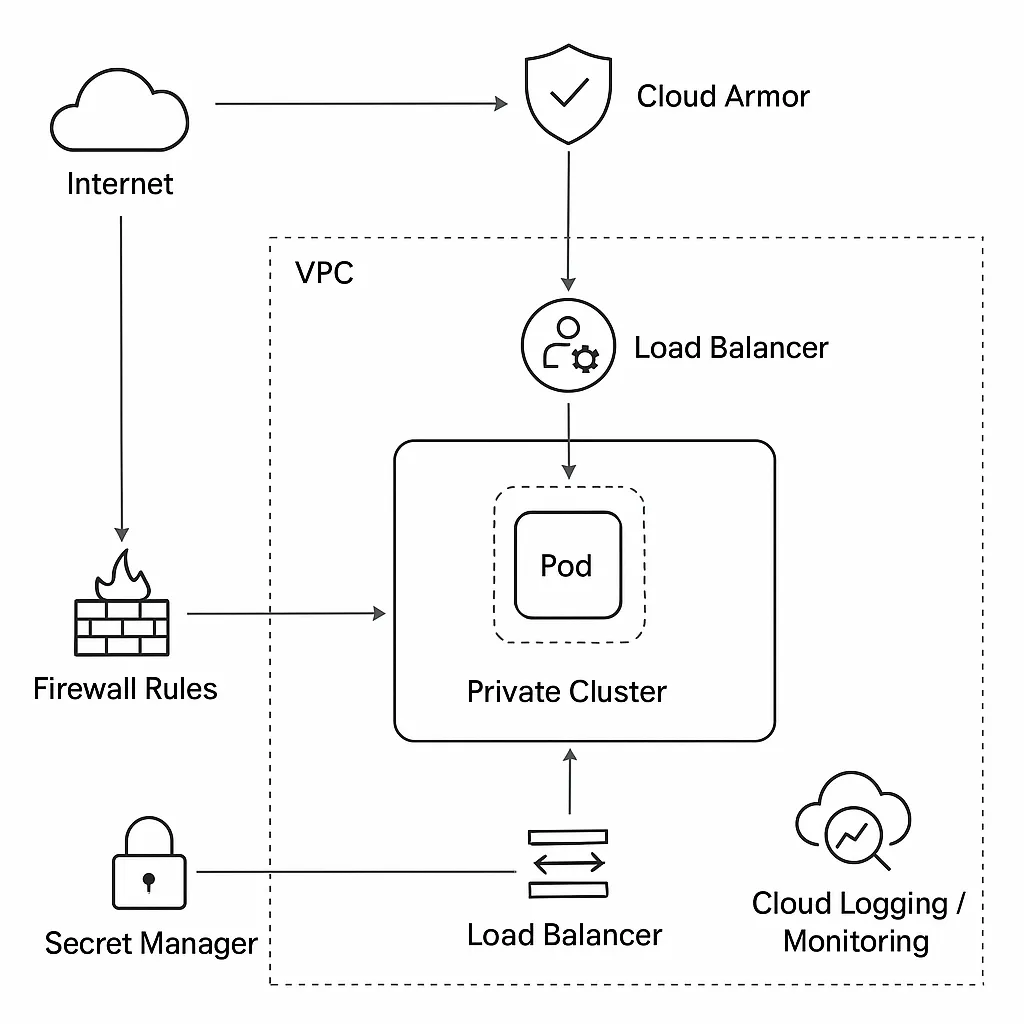
Table of Contents
Secure GKE Deployment
This project involved architecting and implementing a hardened deployment pipeline for a Google Kubernetes Engine (GKE) web application, achieving enterprise-grade security across identity, infrastructure, network, and workload layers.
This Secure GKE Deployment leveraged Cloud Armor (WAF/DDoS), IAM, private GKE clusters, and Network Policies to meet cloud security best practices.

Key Components & Configuration Highlights
- Secure GKE Cluster: Implemented a private cluster with restricted access and used Workload Identity for secure service-to-service communication instead of Kubernetes secrets.
- Least Privilege IAM: Audited and tightened user and service account permissions, using custom roles where needed and enforcing 2FA.
- Cloud Armor Protection: Deployed as a Web Application Firewall (WAF) and DDoS protection, utilizing OWASP rules and custom filters.
- Isolated Network: Configured a private Google Cloud VPC with specific firewall rules and Network Policies to control traffic within the GKE cluster.
- Secure Secrets Management: Used Google Cloud Secrets Manager to store and manage sensitive information like API keys.
- Comprehensive Monitoring: Enabled Google Cloud Operations Suite for detailed logging of application and security events, along with custom alerts.
Testing & Validation
- Vulnerability Scanning: Used Google Cloud’s Container Analysis to identify potential weaknesses in container images.
- Firewall Verification: Confirmed the effectiveness of firewall rules using command-line tools and VPC Flow Logs.
- Simulated Penetration Testing: Conducted controlled attacks to test the security measures, including attempts to bypass access controls and the WAF.
Outcomes & Value Delivered
Business Impact
This project significantly strengthened the security posture of the GKE-hosted web application, minimizing its vulnerability to attacks and ensuring business continuity. Implementing robust access controls and network segmentation reduced the risk of data breaches and unauthorized access. Integrating WAF and DDoS protection ensures the application’s availability and protects against common web threats, contributing to a more reliable and trustworthy service for users.
Key Security Gains
The hardened GKE environment achieved a smaller attack surface, making it significantly more resilient to threats. Granular IAM controls limited the potential impact of compromised accounts. Cloud Armor provides robust protection against web application vulnerabilities and DDoS attacks. Network Policies enforced micro-segmentation, containing potential breaches. Comprehensive logging and alerting enabled proactive threat detection and faster incident response.
Skills Leveraged & Enhanced
This project directly applied and further developed my expertise in:
- Cloud-Native Security Architecture: Designing and implementing secure solutions within Google Cloud, explicitly leveraging GKE.
- Kubernetes Security Hardening: Implementing best practices to secure containerized applications and the underlying GKE infrastructure.
- DevSecOps Implementation: Integrating security controls early in the deployment pipeline using IAM, WAF, and secure networking principles.
- Network Security in the Cloud: Configuring and managing Google Cloud VPC, Firewall Rules, and Network Policies for granular control.
- Identity and Access Management (IAM):: Implementing and auditing fine-grained permissions to enforce the principle of least privilege.
- Security Testing and Validation: Utilizing GCP tools and methodologies to verify the effectiveness of implemented security controls.