Fortigate Firewall Optimization: Reducing Attack Surface by 40%
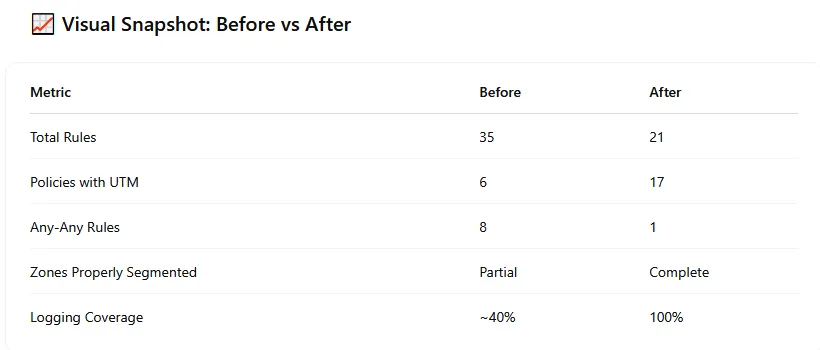
Table of Contents
Fortigate Firewall Optimization
This project involved conducting a comprehensive security audit to optimize a small business security infrastructure. The primary goal was to reduce the attack surface by cleaning up the firewall rule base while enhancing security through tightened access control, Unified Threat Management (UTM) profiles, and improved logging.
The result was a 40% reduction in firewall rules, elimination of risky open services, and ensured proper network segmentation.

Key Components & Configuration Highlights
- FortiGate Firewall (60F): Focused on optimizing the configuration of an edge firewall commonly used by small to mid-sized businesses.
- Firewall Rules Review & Refinement: Analyzed existing 35 firewall policies, identifying and addressing overly permissive, redundant, and outdated rules.
- UTM Profile Application: Implemented and recommended using FortiGate’s Unified Threat Management (UTM) profiles (Antivirus, IPS, Web Filtering, Application Control) on relevant policies to bolster defense-in-depth.
- Zone Segmentation Enforcement: Ensured clear separation and restricted traffic flow between Internal, DMZ, and Guest Wi-Fi zones based on the principle of least privilege.
- Logging Enhancement: Enabled and recommended logging on critical traffic policies for improved security visibility and troubleshooting.
- Remote Admin Restriction: Tightened access for remote administration, suggesting fixed IPs and Multi-Factor Authentication (2FA).
Testing & Validation
- Rule Reduction: Decreasing the number of rules suggests successful consolidation and removing inefficiencies.
- Blocked Services: Identifying and blocking high-risk services indicates a functional improvement in the security posture.
- Logging Coverage: The increase to 100% logging on sensitive traffic implies verification of the logging configuration.
- UTM Application: The increased number of policies with UTM profiles suggests successful implementation of these security features.
Outcomes & Value Delivered
Business Impact
By streamlining the Fortinet firewall rule base by 40%, this project simplified network management and reduced the potential for misconfigurations, improving operational efficiency. Blocking unnecessary high-risk services and implementing comprehensive UTM profiles significantly strengthened the organization’s defense against external threats, minimizing the risk of costly security incidents and data breaches. Enhanced logging on all sensitive traffic provides crucial visibility for proactive threat detection and faster incident response, ensuring business continuity and regulatory compliance.
Key Security Gains
The optimized firewall now presents a significantly smaller and more manageable attack surface. Implementing granular control through refined rules and proper network segmentation limits the lateral movement of threats, containing potential breaches. The application of Fortinet’s UTM features (Antivirus, IPS, Web Filtering, Application Control) provides multi-layered protection against a wide range of cyber threats. Comprehensive logging ensures security events are captured and can be analyzed for proactive threat hunting and effective incident response.
Skills Leveraged & Enhanced
This project directly utilized and further honed my expertise in:
- Strategic Firewall Management: Analyzing and optimizing complex Fortinet firewall configurations using CLI and GUI for enhanced security and manageability.
- Security Rule-base Optimization: Employing proven techniques to identify and eliminate redundant, overly permissive, and outdated rules, improving performance and security.
- Threat Prevention Implementation: Deep understanding and practical application of Fortinet’s UTM profiles to provide robust protection against various threat vectors.
- Network Segmentation Design: Implementing and validating network zoning principles to isolate critical assets and limit the impact of security incidents.
- Security Visibility and Analysis: Configuring and leveraging logging and monitoring capabilities to gain critical insights into network traffic and potential security events.
- Security Best Practices & Compliance: Applying CISSP-aligned security principles, such as least privilege, throughout the optimization process to ensure adherence to industry standards.